Organizational Security Policy
The organizational security policy is the document that defines the scope of a utility’s cybersecurity efforts. It serves as the repository for decisions and information generated by other building blocks and a guide for making future cybersecurity decisions. The organizational security policy should include information on goals, responsibilities, structure of the security program, compliance, and the approach to risk management that will be used.
Importance
The organizational security policy serves as a reference for employees and managers tasked with implementing cybersecurity. What has the board of directors decided regarding funding and priorities for security? What new security regulations have been instituted by the government, and how do they affect technical controls and record keeping? Which approach to risk management will the organization use? How will the organization address situations in which an employee does not comply with mandated security policies?
The organizational security policy serves as the “go-to” document for many such questions. It expresses leadership’s commitment to security while also defining what the utility will do to meet its security goals.
Intersections With Other Building Blocks
Because the organizational security policy plays a central role in capturing and disseminating information about utility-wide security efforts, it touches on many of the other building blocks. The governance building block produces the high-level decisions affecting all other building blocks. The compliance building block specifies what the utility must do to uphold government-mandated standards for security. The organizational security policy captures both sets of information.
The utility’s approach to risk management (the framework it will use) is recorded in the organizational security policy and used in the risk management building block to develop a risk management strategy. Objectives defined in the organizational security policy are passed to the procurement, technical controls, incident response, and cybersecurity awareness training building blocks.
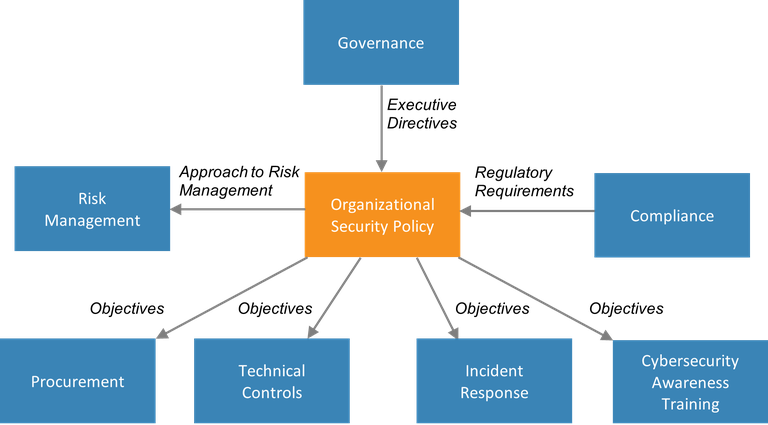
Figure 2. Information passed to and from the organizational security policy building block
Process and Actions
Developing an organizational security policy requires getting buy-in from many different individuals within the organization. The policy needs an “owner”—someone with enough authority and clout to get the right people involved from the start of the process and to see it through to completion. The owner will also be responsible for quality control and completeness (Kee 2001). Appointing this policy owner is a good first step toward developing the organizational security policy.
The policy owner will need to identify stakeholders, which will include technical personnel, decision makers, and those who will be responsible for enforcing the policy. Ideally, the policy owner will be the leader of a team tasked with developing the policy. Everyone must agree on a review process and who must sign off on the policy before it can be finalized.
The utility decision makers—board, CEO, executive director, and so on—must determine the business objectives that the policy is meant to support and allocate resources for the development and implementation of the policy. Business objectives should drive the security policy—not the other way around (Harris and Maymi 2016).
The utility will need to develop an inventory of assets, with the most critical called out for special attention. Threats and vulnerabilities should be analyzed and prioritized. Mitigations for those threats can also be identified, along with costs and the degree to which the risk will be reduced.
The policy will identify the roles and responsibilities for everyone involved in the utility’s security program. The utility leadership will need to assign (or at least approve) these responsibilities. Objectives for cybersecurity awareness training objectives will need to be specified, along with consequences for employees who neglect to either participate in the training or adhere to cybersecurity standards of behavior specified by the organization (see the cybersecurity awareness training building block for more details).
The policy can be structured as one document or as a hierarchy, with one overarching master policy and many issue-specific policies (Harris and Maymi 2016). The SANS Institute offers templates for issue-specific policies free of charge (SANS n.d.); those templates include:
- Acceptable encryption policy
- Data breach response policy
- Internet usage policy
- Remote access policy
- Risk assessment policy
- Social engineering awareness policy
- Virtual private network policy.
When the policy is drafted, it must be reviewed and signed by all stakeholders. A cycle of review and revision must be established, so that the policy keeps up with changes in business objectives, threats to the organization, new regulations, and other inevitable changes impacting security.
Essential Data
The following information should be collected when the organizational security policy is created or updated, because these items will help inform the policy.
- A list of stakeholders who should contribute to the policy and a list of those who must sign the final version of the policy
- An inventory of assets prioritized by criticality
- Historical data on past cyberattacks, including those resulting from employee errors (such as opening an infected email attachment). This will supply information needed for setting objectives for the cybersecurity awareness training building block.
- Threats and vulnerabilities that may impact the utility.
In addition, the utility should collect the following items and incorporate them into the organizational security policy:
- Business objectives (as defined by utility decision makers)
- Laws, regulations, and standards applicable to the utility, including those focused on safety, cybersecurity, privacy, and required disclosure in the case of a successful cyberattack.
Webinars
Developing a robust cybersecurity defense program is critical to enhancing grid security and power sector resilience. Creating an Organizational Security Policy helps utilities define the scope and formalize their cybersecurity efforts. Developed in collaboration with CARILEC and USAID, this webinar is the next installment in the Power Sector Cybersecurity Building Blocks webinar series and features speakers from Deloitte, NREL, SKELEC, and PNM Resources to speak to organizational security policy’s critical importance to utility cybersecurity.
Watch a webinar on Organizational Security Policy.
References
Harris, Shon, and Fernando Maymi. 2016. CISSP All-in-One Exam Guide 7th ed. New York: McGraw Hill Education.
Recommended Reading
IBM Knowledge Center. “Developing a Security Policy.” October 24, 2014.
Kee, Chaiw. 2001. Security Policy Roadmap - Process for Creating Security Policies. SANS Institute.
SANS. “Security Policy Templates.” Accessed December 30, 2020.
Additional Resources
Duigan, Adrian. “10 Steps to a Successful Security Policy.” Computerworld. October 8, 2003.
Ng, Cindy. “How to Create a Good Security Policy.” Inside Out Security (blog). March 29, 2020.
Wood, Charles Cresson. 2002. Information Security Policies Made Easy 9th ed. PentaSafe Security Technologies.






