Cybersecurity Building Blocks
The Cybersecurity Building Blocks consist of eleven concise resources, each discussing a particular element of a well-rounded cybersecurity framework their importance, how they intersect and support each other, processes and actions associated with each building block, and data essential to each. The resources also include case studies showing the value of each Cybersecurity Building Block and references for more information.
The Cybersecurity Building Blocks are meant to be a starting point for utilities to promote a more rounded approach to cybersecurity that addresses both the technical and managerial requirements for protecting critical infrastructure.
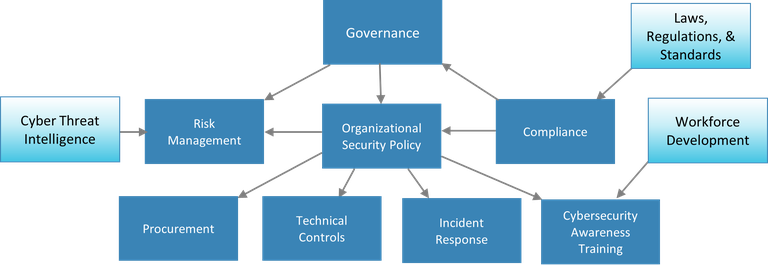
Governance
The governance building block covers the processes that direct a utility-wide cybersecurity effort and provide accountability for that effort. Cybersecurity ...
Organizational Security Policy
This building block focuses on the high-level document that captures the essential elements of a utility’s efforts in cybersecurity and includes the effort to ...
Risk Management
The risk management building block encompasses activities that identify and evaluate cybersecurity risk, with the goal of reducing that risk to a level ...
Cyber Threat Intelligence (CTI)
Cyber Threat Intelligence consists of cyberattack tools and adversaries that might constitute a threat and the vulnerabilities they could exploit. Utilities ...
Laws, Regulations, and Standards
Laws and regulations are the compulsory host country directives that a utility must comply with regarding cybersecurity. Regulations sometimes enforce ...
Compliance
Compliance is the effort within a utility to remain in compliance with laws, regulations, and standards.
Procurement
Procurement is the processes used to monitor and improve the cybersecurity of devices, applications, and services as they are acquired and integrated into ...
Technical Controls
Technical controls consist of the hardware and software components that protect a system against cyberattack. Firewalls, intrusion detection systems (IDS), ...
Incident Response
The actions taken by a utility to prepare for cyberattacks are incident response. This includes creating plans for response, rehearsing the response prior to ...
Cybersecurity Awareness Training
Cybersecurity awareness training consists of steps taken by utilities to educate all employees (including nontechnical staff) about potential cyber threats and ...
Workforce Development
The efforts by multiple organizations, such as government, industry, or academia, to ensure an adequate supply of workers with specialized cybersecurity ...






